First, let me start that if you want a lot of people to download something, make sure that the words "HTML5," "Support" and "Update" appear in the title. I'm sure if the folks that are making Diablo 3 called it "Diablo 3 HTML5 Support Update" that a metric buttload more people would download it. That said, a bunch of folks in the Web Platform and Tools team created the Web Standards Update package with HTML5 Support for the Visual Studio 2010 Editor.This Web Standards Update is something that anyone in the community could have released, just extending Visual Studio in a standard way. Like many other (most) extensions in Visual Studio Extension Gallery, it was not "signed." It was not a formal project done by Microsoft. Ratherthis was something that a bunch of us did for the community in our after work hours. The only reason why this got in spotlight was because press caught the wind of it having HTML5 and CSS3 support. Certainly a lot of people wanted it because in 4 days it's now the #1 most popular thing in the Visual Studio Gallery. Take that NuGet! ;)Here's where the trouble starts. Then, it was written about in the press as if it were a "gaffe." I admit that we (mostly I) did a lousy mediocre job of making it clear that this update was a "community update from the inside," as it were. It's not official, but we're hoping support like this will make its way into the next version of Visual Studio. When you downloaded the MSI installer with IE9, as with all MSIs that aren't signed, you get a message like this:
And that's normal and quite lovely. Then we see this scary red bar (this is a shot from another gallery item):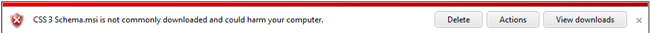
This is the IE9 SmartScreen system warning us, rightfully so, that this is not something downloaded all the time. In fact, this is a really useful feature of IE9 and is fairly unique amongst the browsers so far. It's using some special sauce (some hash, some math, some metrics) to make a non-biased judgment about this download. Even though it's coming from a Microsoft.com website it doesn't matter. SmartScreen is unbiased. It's never seen this before, and it's not trusted. UPDATE: Looks like as of my test just now that SmartScreen now recognizes our download as safe!
Read more: Scott Hanselman Computer Zen
QR:


Read more: Scott Hanselman Computer Zen
QR: