One-time pads are the holy grail of cryptography—they are impossible to crack, even in principle.
They work by adding a set of random digits to a message thereby creating a ciphertext that looks random to any eavesdropper. The receiver decodes the message by taking away the same set of random digits to reveal the original message.
The security of this process depends on two factors. The first is the randomness of the digits that make up the one-time pad. If this key is truly random, it offers nothing the eavesdropper can use to break the code. Although there are some potential pitfalls, random digits are reasonably straightforward to generate these days.
The second factor is the ability to keep this key secret so that only the transmitter and receiver have access to it. That's much more difficult to ensure.
Digital communication in the form of 0s and 1s makes copying trivial. Whenever a set of random digits is stored in an electronic memory, there is always a small but finite chance that it can be quickly copied and stolen.
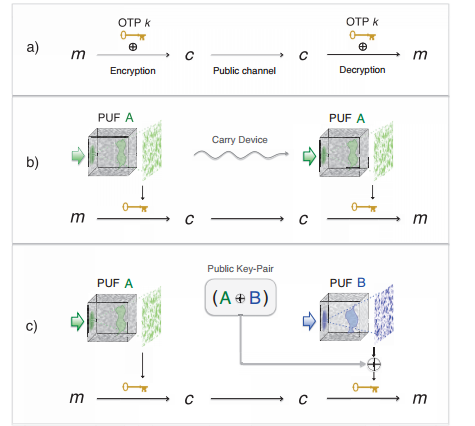
Today, Roarke Horstmeyer at the California Institute of Technology in Pasadena and a few buddies say they've solved this problem. Their solution is based on a special kind of one-time pad that generates a random key through the complexity of its physical structure.
Instead of creating and storing the one-time pad as a random sequence of 0s and 1s, Horstmeyer and co generate a random signal by passing light through a slab of diffusing glass that scatters it randomly.
The security of the system depends on the physical complexity of the glass. Horstmeyer and co say that that this complexity means there is no way for an eavesdropper, "Eve," to copy the glass without anyone noticing.
That cuts out the need to store the key electronically and entirely removes this vulnerability to copying. "We describe an encrypted communication principle that can form a perfectly secure link between two parties without electronically saving either of their keys," they say
Read more: MIT Technology Review
QR: 